Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
 Read MoreBecome a Security Analyst: Protect Digital Assets
Read MoreBecome a Security Analyst: Protect Digital Assets Read MoreSecurity Architect: Safeguarding Digital Landscapes
Read MoreSecurity Architect: Safeguarding Digital Landscapes Read MoreWhy More People Are Using App Blockers in 2024
Read MoreWhy More People Are Using App Blockers in 2024 Read MorePop-Up Ad Blockers and YouTube: How to Block Ads Without Disrupting Video Content
Read MorePop-Up Ad Blockers and YouTube: How to Block Ads Without Disrupting Video Content Read MoreSecuring Your Family’s Smartphones and Laptops During Vacation: A Complete Guide
Read MoreSecuring Your Family’s Smartphones and Laptops During Vacation: A Complete Guide Read MoreNord VPN Deals: Save Big on Premium VPN Service
Read MoreNord VPN Deals: Save Big on Premium VPN Service Read MoreBecome a Security Engineer: Protect Digital Assets
Read MoreBecome a Security Engineer: Protect Digital Assets Read MoreChief Technology Officer: Leading Tech Innovation
Read MoreChief Technology Officer: Leading Tech Innovation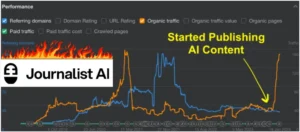 Read MoreJournalist AI Review: Transforming News Creation & Blog Writing
Read MoreJournalist AI Review: Transforming News Creation & Blog Writing Read MoreWhite House Cyber Initiative Seeks to Fill 500000 Cybersecurity Jobs
Read MoreWhite House Cyber Initiative Seeks to Fill 500000 Cybersecurity Jobs Read MoreIndia to Train 5000 Cyber Commandos to Combat Cyber Threats
Read MoreIndia to Train 5000 Cyber Commandos to Combat Cyber Threats Read MoreMicrosoft Hosts Cybersecurity Summit Following Major IT Outage
Read MoreMicrosoft Hosts Cybersecurity Summit Following Major IT Outage Read MoreChief Information Security Officer: Cybersecurity Lead
Read MoreChief Information Security Officer: Cybersecurity Lead Read MoreCIO: Essential Role in Modern Business Leadership
Read MoreCIO: Essential Role in Modern Business Leadership Read MoreCTO: Key Roles and Responsibilities in Tech Leadership
Read MoreCTO: Key Roles and Responsibilities in Tech Leadership Read MoreSave Big with Nord VPN Coupons – Exclusive Deals
Read MoreSave Big with Nord VPN Coupons – Exclusive Deals Read MoreCISO: Essential Role in Cybersecurity Leadership
Read MoreCISO: Essential Role in Cybersecurity Leadership Read MoreExplore Exciting Cyber Careers: Your Digital Future
Read MoreExplore Exciting Cyber Careers: Your Digital Future Read MoreNord VPN Review: Secure & Fast VPN Service
Read MoreNord VPN Review: Secure & Fast VPN Service Read MoreExplore Exciting Cyber Jobs: Launch Your Tech Career
Read MoreExplore Exciting Cyber Jobs: Launch Your Tech Career Read MoreBoost Your Cyber Skills: Expert Tips & Techniques
Read MoreBoost Your Cyber Skills: Expert Tips & Techniques Read MoreFuzzing: Discover Software Vulnerabilities Easily
Read MoreFuzzing: Discover Software Vulnerabilities Easily Read MoreSecurity Testing: Safeguarding Your Digital Assets
Read MoreSecurity Testing: Safeguarding Your Digital Assets Read MoreAttack Simulation: Strengthen Your Cyber Defenses
Read MoreAttack Simulation: Strengthen Your Cyber Defenses Read MorePurple Team: Enhancing Cybersecurity Defense
Read MorePurple Team: Enhancing Cybersecurity Defense Read MorePatient Engagement Technologies – The Best Solution to Connect with Patients
Read MorePatient Engagement Technologies – The Best Solution to Connect with Patients Read MoreBlue Team: Cybersecurity’s First Line of Defense
Read MoreBlue Team: Cybersecurity’s First Line of Defense Read MoreRed Team: Enhancing Cybersecurity Through Testing
Read MoreRed Team: Enhancing Cybersecurity Through Testing Read MoreCyber Ranges: Boost Your Cybersecurity Skills Today
Read MoreCyber Ranges: Boost Your Cybersecurity Skills Today Read MoreBest NordVPN Server for Torrents: Top Choices
Read MoreBest NordVPN Server for Torrents: Top Choices