Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124

Protect your business from cyber threats and physical risks. Hire a security consultant to assess vulnerabilities, implement safeguards, and enhance your overall security posture.

Discover how to become a security analyst and safeguard digital assets. Learn essential skills, certifications, and career paths in this growing cybersecurity field.

Discover the role of a security architect in protecting digital assets. Learn how these experts design robust cybersecurity strategies for organizations.

According to RescueTime, individuals now spend an average of four hours on their mobiles, checking them at least 150 times daily. In another place, a global outplacement agency reported that employers lost up to $14bn in productivity over a 17-week…

YouTube is one of the biggest video sharing websites that encompasses different types of videos including tutorials, music, documentary and many more. Moreover, ads can appear quite often, and this can be quite frustrating when one is watching his/her favourite…

Vacations are a time to unwind, explore new locations, and build lasting memories with loved ones. But have you ever considered how vulnerable your digital devices might be while you’re away? In an increasingly connected world, smartphones and laptops have…

Discover exclusive NordVPN deals and secure your online privacy for less. Get top-tier protection, fast speeds, and global server access at unbeatable prices.

Discover how to become a security engineer and safeguard digital assets. Learn essential skills, certifications, and career paths in this growing field of cybersecurity.

Discover the role of a Chief Technology Officer in driving innovation and shaping tech strategy. Learn how CTOs lead digital transformation and engineering excellence.
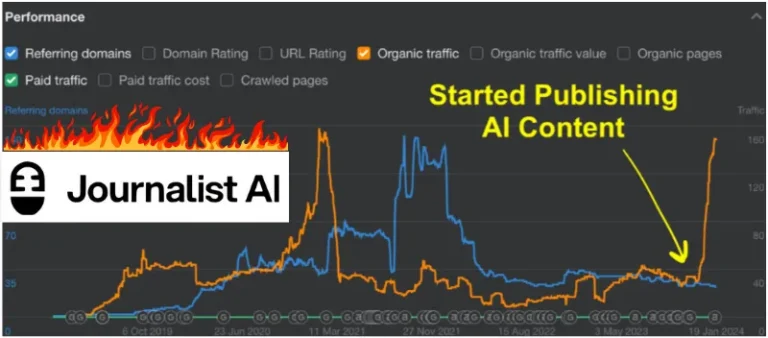
Discover how AI is revolutionizing journalism and blog writing. Our Journalist AI Review explores cutting-edge tools that enhance content creation and streamline workflows.