Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
As a web developer, you know how crucial it is to make apps that keep your users’ data safe. But, with new cyber threats popping up all the time, it’s tough to keep up. That’s where the OWASP Top 10 comes in – a key guide that highlights the main security risks for web apps1.
In today’s world, web app security is a top concern. The OWASP Top 10 is a vital tool for developers, security experts, and companies. It helps you build apps that are strong, reliable, and can handle even the toughest attacks2.
The OWASP Top 10 is key in web application security. It highlights the top security risks for web apps3. The list changes often to match new threats, with the newest version coming out in 2021. This marks 20 years of OWASP’s work.
A team leads the OWASP Top 10 project. They use data from many sources, like security companies and bug bounties3. The goal is to spotlight major web application vulnerabilities. It helps companies focus on fixing these issues.
The OWASP Top 10 is a top guide for web app security4. It lists the most critical security risks. This helps developers and companies make their apps safer.
By fixing these issues, companies can lower the chance of data breaches4.
OWASP also has tools like the OWASP Bug Logging Tool (BLT) to help improve internet security4. They invite people to join, attend meetings, and go to events. This helps professionals learn and connect in the field4.
The OWASP Top 10 list has seen big changes to match the changing web security needs5. These updates aim to give better advice and tackle new threats to web apps.
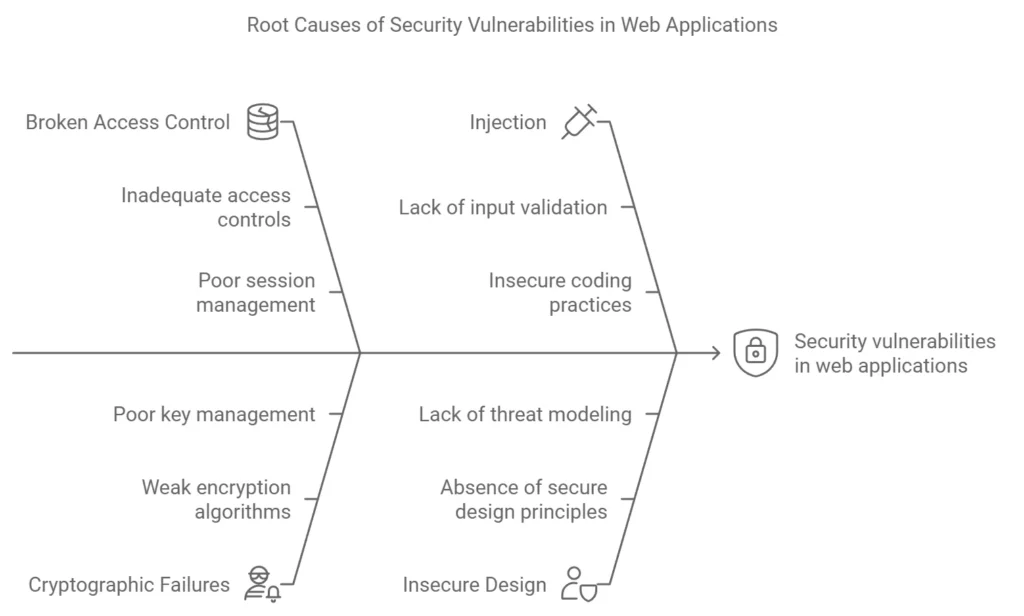
The 2021 OWASP Top 10 has new categories and changes to old ones5. Broken Access Control is now the top concern, showing its big impact6. This issue was found in many apps, with 3.81% having a related weakness7.
“Sensitive Data Exposure” is now called “Cryptographic Failures.”5 This change highlights the need for strong crypto controls to keep data safe6. Cryptographic Failures are now the second biggest concern on the list.
The 2021 list adds “Insecure Design” and “Software and Data Integrity Failures” as new categories5. These focus on design flaws and keeping software and data safe7. Categories like “Injection” and “Security Misconfiguration” were merged for clearer advice5.
The updates show how web app security threats are changing and we need a broader approach7. The list now focuses on the main issues, helping organizations focus their security efforts5.
The OWASP Top 10 is key for web app developers and security experts to keep up with security5. Knowing the 2021 changes helps them update their security plans to meet new threats6.
The OWASP Top 10 for 2021 has put Broken Access Control at the top, showing its importance. On average, 3.81% of apps tested had issues with broken access control. This means 318,487 problems were found across 34 types8. This shows why fixing this issue is urgent for companies.
Broken Access Control can lead to big problems. Attackers can get into places they shouldn’t, take over, and mess with how things work. In 2014, a big leak happened because of this in Snapchat, exposing 4.6 million users’ info9. To stop this, using strong access controls like RBAC and the Principle of Least Privilege is key9.
Broken Access Control is a big deal, also in API Security Top 10 by OWASP. The first 6 issues are about broken login or permission controls10. Hackers use tricks like changing URLs, messing with cookies, or pretending to be someone else to get into systems10.
To fix these problems, companies should work on secure login, deny access unless allowed, and manage sessions safely. They should also limit how many attempts can be made to get in10. It’s also important to always check user input to stop attacks from bad data handling10.
By tackling Broken Access Control and focusing on web app security, companies can lower the risk of unauthorized access and data breaches8910.
Cryptographic Failures, now called Sensitive Data Exposure, is the #2 threat on the OWASP Top 10 list for 2021. This change shows how important it is to handle cryptography well. It can lead to sensitive data being exposed or systems being compromised11.
Weak encryption algorithms, poor key management, and insecure communication are main causes of these failures. These issues can make sensitive data easy to access and use wrongly12.
Attackers often target weak spots in encryption algorithms and keys. Not encrypting data well and not checking server certificates can also lead to problems12.
To fix these issues, it’s key to use strong encryption, manage keys well, and secure communication in web apps. This means encrypting data both when it’s stored and when it’s moving, using strong encryption types, and updating old encryption methods12.
Also, avoid storing sensitive data in caches and make sure passwords are safely stored. The best way to fix these problems will vary based on the company and the specific issues found12.
By tackling cryptographic failures early, companies can lower the risk of data breaches and system problems. This makes their web apps more secure11.
| Metric | Value |
|---|---|
| CWEs Mapped | 29 |
| Max Incidence Rate | 46.44% |
| Avg Incidence Rate | 4.49% |
| Avg Weighted Exploit | 7.29 |
| Avg Weighted Impact | 6.81 |
| Max Coverage | 79.33% |
| Avg Coverage | 34.85% |
| Total Occurrences | 233,788 |
| Total CVEs | 3,075 |
Injection vulnerabilities have moved to the third spot in the OWASP Top 10 2021 list. Yet, they still pose a big threat13. About 94% of apps tested had injection vulnerabilities, with a peak of 19.09% and an average of 3.37%13. These flaws led to 274,228 reported incidents, making them the second most common type13.
Now, the injection category includes Cross-Site Scripting (XSS) attacks. This highlights the need for good input validation and sanitization to stop injection threats13.
Injection flaws, like SQL injection and XSS, are a big part of web app security risks14. SQL injection is the top injection type, making up 65% of incidents, while XSS is about 25%14.
Injection flaws have a big impact, causing 20% of data breaches and unauthorized access14. But, strong input validation and output encoding can cut the risk of attacks by up to 70%. WAFs and RASP technologies can block 80% of injection attempts14.
Regular security checks, like penetration testing and code reviews, find and fix about 90% of injection flaws in web apps14. With injection vulnerabilities still key in the OWASP Top 10 2021, it’s vital for developers and security pros to focus on fixing these issues15.
| Metric | Value |
|---|---|
| CWEs Mapped | 33 |
| Max Incidence Rate | 19.09% |
| Average Incidence Rate | 3.37% |
| Average Weighted Exploit | 7.25 |
| Average Weighted Impact | 7.15 |
| Max Coverage | 94.04% |
| Average Coverage | 47.90% |
| Total Occurrences | 274,228 |
| Total CVEs | 32,078 |
Insecure Design is now a key focus in the 2021 OWASP Top 10. It shows how vital it is to think about security early on in making software16. To improve security, we need to use threat modeling, secure design patterns, and reference architectures more16.
An insecure design can’t be fixed later with just a good implementation. The security controls needed to fight attacks were missing from the start17. It’s key to use secure design principles right from the beginning. This makes it easier to keep software safe16.
Using secure design patterns and principles helps keep software safe over time16. Regular checks and tests can spot design issues that could lead to security problems16. Having a focus on security early on is crucial for making secure software16.
Insecure Design is a new area that covers17 40 CWEs. It has a top rate of 24.19% and an average of 3.00%17. The exploit and impact scores average at 6.46 and 6.78, with coverage at 77.25% and 42.51%17. This focus on design security aims to tackle issues from the start of software creation16.
Security Misconfiguration has become more important in the OWASP Top 10 for 2021. It moved up from the 6th spot to a higher position. This change is because 90% of applications tested had misconfigurations, with an average of 4.51%21.
This issue is a big problem for web applications, making it crucial for developers and security experts to tackle it.
Common mistakes include not removing default accounts and passwords, not securing cloud storage, and wrong web server settings22. These errors happen for many reasons, like too many privileges, unnecessary features, and missing security headers22.
Fixing these misconfigurations is key to keeping web applications safe. To improve security, turn off unused features, follow the Principle of Least Privilege, and set up security headers correctly22. It’s also important to keep services and packages updated and do regular security checks22.
Checking infrastructure often and doing penetration tests can also spot and fix security issues in web applications22.
“Security Misconfiguration is a critical vulnerability that can have far-reaching consequences for web applications. By addressing common misconfigurations and implementing best practices, organizations can significantly improve the overall security of their digital assets.”
In the world of web app security, vulnerable components are now the #6 concern on the OWASP Top 10 list23. This issue, once called “Using Components with Known Vulnerabilities,” has grown more common. Companies find it hard to keep track of the risks from these components23.
This problem doesn’t have any Common Vulnerability and Exposures (CVEs) linked to the included CWEs. So, a default exploit and impact score of 5.0 is used in their ratings24.
This shows how crucial it is to have a strong dependency management system. It’s also key to watch for security updates to avoid software vulnerabilities in your web app’s software supply chain23.
To tackle this, scan your web apps for vulnerabilities often. Keep an updated list of third-party components. And apply security updates quickly from developers23.
Don’t use components that haven’t been updated recently or have no active developers. These can lead to security risks like SQL injection, cross-site scripting, and remote code execution23.
| Metric | Value |
|---|---|
| CWEs Mapped | 3 |
| Max Incidence Rate | 27.96% |
| Avg Incidence Rate | 8.77% |
| Max Coverage | 51.78% |
| Avg Coverage | 22.47% |
| Avg Weighted Exploit | 5.00 |
| Avg Weighted Impact | 5.00 |
| Total Occurrences | 30,457 |
| Total CVEs | 0 |
For more on this topic, check out the detailed analysis at Vulnerable and Outdated Components in Web24. By knowing the risks and taking steps ahead, you can make your web apps more secure. This protects your users from threats23.
Identification and authentication failures, also known as “Broken Authentication,” are a big deal. They’re now part of the OWASP Top 10. This includes weak passwords, missing multi-factor authentication, and poor password policies25. These issues can cause big problems like unauthorized access and data breaches.
Poor password management and using easy-to-guess passwords are big reasons for these failures26. Hackers use brute-force attacks and credential stuffing to get into systems. Not having multi-factor authentication (MFA) makes it easy for them to pretend to be someone else.
To stop these problems, companies should use strong password rules, require MFA, and manage credentials safely26. Watching and logging who logs in can also help spot and solve security issues26.
These issues used to be the #2 problem in 2017 but are now #7 in the 2021 OWASP Top 10 list27. But they’re still a big worry. Hackers can use many tricks, like brute force and session hijacking, to get into systems27.
Using strong security steps, like MFA and safe password storage, can help fix these problems26. It’s also a good idea to test your apps regularly to find and fix these issues. This makes apps and users safer27.
The OWASP Top 10 for 2021 introduces a new category, “A08:2021-Software and Data Integrity Failures.” It highlights the need to check the integrity of software, updates, and important data28.
This category covers 10 Common Weakness Enumeration (CWE) issues, with a top rate of 16.67% and an average of 2.05%28. The scores for exploit and impact average at 6.94 and 7.94, showing the big risk these weaknesses bring28.
Supply chain attacks are a big worry in this area. These attacks can compromise the integrity of software or updates, adding malicious code or data29. For instance, the 2017 WannaCry ransomware hit over 230,000 computers in more than 150 countries, causing losses of $80 million to $1 billion29.
To fight these risks, companies must have strong checks for software, updates, and key data29. This means watching updates, applying security patches quickly, and using tools like Software Bill of Materials (SBOM) and Software Composition Analysis (SCA) to spot and handle vulnerable parts29. Keeping updates and patches up to date helps protect CI/CD pipelines and the overall software integrity29.
| Metric | Value |
|---|---|
| CWEs Mapped | 10 |
| Max Incidence Rate | 16.67% |
| Avg Incidence Rate | 2.05% |
| Avg Weighted Exploit | 6.94 |
| Avg Weighted Impact | 7.94 |
| Max Coverage | 75.04% |
| Avg Coverage | 45.35% |
| Total Occurrences | 47,972 |
| Total CVEs | 1,152 |
By tackling software and data integrity failures, companies can boost their security and shield their systems and data from threats like supply chain attacks2829.
The “A09:2021-Security Logging and Monitoring Failures” category is now more important, moving up to the 9th spot in the 2021 OWASP Top 10. It covers issues from not logging enough, not checking logs, and not catching security problems on time30.
Not logging security events and not watching logs can really hurt an organization. It makes it hard to know what’s happening, alert others to problems, and figure out what went wrong30.
Not logging things like failed login tries or changes to system settings is a big mistake. Not watching for odd log entries or sudden system changes is another30.
Also, losing logs too soon makes it tough to solve past security issues. And if logging and monitoring aren’t secure, attackers might get into or change the logs, making it harder to track them30.
To fix these issues, companies need strong logging and monitoring setups30. This means logging all important security events and keeping log files safe. It also means checking logs often, setting up alerts, having a plan for when things go wrong, and always getting better at logging and monitoring30.
The OWASP Top 10 2021 says this issue is hard to test and isn’t well-covered in CVE/CVSS data. But, it could cause a lot of damage, with high exploit and impact scores31. Security logging and monitoring failures have been found in 53,615 cases across 242 CVEs, showing how widespread the problem is31.
Having good security logging and monitoring is key for companies. It helps them see what’s happening, deal with problems fast, and investigate security issues well. By fixing the problems and taking steps to prevent them, companies can get better at protecting against cyber threats30.
Server-Side Request Forgery (SSRF) is a web application vulnerability now in the OWASP Top 10 2021 list, at number 1032. It lets attackers access internal resources without permission, exposing data and causing security issues33.
SSRF has a 2.72% max and average incidence rate in CWEs, showing its impact33. It also has an average exploit and impact rating of 8.28 and 6.72, highlighting its threat level33.
SSRF can lead to various issues, like IP scanning or accessing hidden IP addresses behind proxies32. It includes direct server interaction and using a compromised system for sensitive info32. SSRF can also cause Remote Code Execution and allow attackers to perform scans or Cross Site Port Attacks (XSPA)32.
The security community has focused on SSRF, with a 67.72% max and average coverage rate33. Despite this, SSRF incidents and related CVEs are still significant, with 9,503 occurrences and 385 CVEs33.
To fight SSRF risks, web developers should validate inputs, limit internal access, and keep systems updated3332.
| Metric | Value |
|---|---|
| Max incidence rate for SSRF in CWEs | 2.72%33 |
| Average incidence rate for SSRF in CWEs | 2.72%33 |
| Average weighted exploit rating for SSRF | 8.2833 |
| Average weighted impact rating for SSRF | 6.7233 |
| Maximum coverage rate for SSRF | 67.72%33 |
| Average coverage rate for SSRF | 67.72%33 |
| Total occurrences of SSRF incidents recorded | 9,50333 |
| Total number of CVEs related to SSRF | 38533 |
In conclusion, SSRF is a key web application vulnerability in the OWASP Top 10 2021 list. It can cause unauthorized access and data exposure, making it crucial for developers and security experts to address.
The34 OWASP Top 10 is key for keeping web apps safe. It lists the top risks and weaknesses that companies must tackle. The 2021 version added34 three new threats and34 combined two others. This helps security experts and developers know where to focus their efforts34.
OWASP Top 10 threats are often simple to exploit and can be stopped before they cause harm. They are easy to find and can have a big impact if not fixed. That’s why it’s important to deal with them quickly34.
Using the OWASP Top 10 and secure coding is vital for protecting web apps and their data34. It’s important for all companies with web apps to test their security regularly. This should include both manual and automated checks by skilled people34.
Putting security tests into the app development process helps stop breaches before they happen. This keeps sensitive data safe34.
The OWASP Top 10 keeps changing, with new areas like Insecure Design added in 202235. We can expect to see more focus on threats like Advanced Supply Chain Attacks and AI/ML Vulnerabilities in 202435. Security experts need to stay alert and update their plans to keep up with web app security changes35.
It’s important to keep working on issues like Injection and Security Misconfiguration. At the same time, embracing new security approaches is key to protecting your web apps.
The OWASP Top 10 is a key guide for developers and web app security. It lists the top security risks for web apps. It helps developers write more secure code and companies should use it to lower these risks.
The OWASP Top 10 is a crucial first step towards better security in your company. It highlights the main threats to web apps and ranks them by importance. This helps companies focus their security efforts and reduce risks.
The 2021 OWASP Top 10 has three new categories and four with changes in name and scope. It focuses on the root cause of issues, like renaming “Sensitive Data Exposure” to “Cryptographic Failures”. New categories include “Insecure Design” and “Software and Data Integrity Failures”, focusing on design flaws and data integrity.
A01:2021-Broken Access Control is now the top risk, moving up from fifth place. On average, 3.81% of apps tested had issues with access control, with over 318k weaknesses found in this area.
A02:2021-Cryptographic Failures is now the second risk, focusing on failures in cryptography. This can lead to data exposure or system breaches. Causes include weak encryption, poor key management, and insecure protocols. To fix this, use strong encryption, manage keys well, and secure communication protocols in web apps.
A04:2021-Insecure Design is a new category for 2021, focusing on design flaws. It’s key to address security early in development. Threat modeling, secure design, and secure architectures are crucial. Insecure design can’t be fixed later, as security controls were never built to defend against attacks.
The OWASP Top 10 categories are chosen based on data and community input. Broken Access Control, Injection, and Security Misconfiguration are common. These issues can lead to serious problems like data breaches and system breaches.
A05:2021-Security Misconfiguration is now more critical, with 90% of apps tested showing misconfigurations. Common issues include default accounts, unsecured cloud storage, and web server misconfigurations. Fixing these is key to web app security.
A07:2021-Identification and Authentication Failures is still vital, despite dropping in rank. Causes include poor password management and weak authentication. To prevent this, use strong passwords, require multi-factor authentication, and secure credentials.
A09:2021-Security Logging and Monitoring Failures is now part of the Top 10, focusing on logging and monitoring. Causes include inadequate logging and monitoring. To prevent this, ensure comprehensive logging, improve monitoring, and have robust security measures in place.
A10:2021-Server-Side Request Forgery is a new addition, focusing on SSRF vulnerabilities. These can let attackers access internal resources, exposing data and causing breaches.